ianya proses transformasi dari plain text (benda yang kita faham) menggunakan key atau chiffer kepada chiffer text (perkataan yang kita tak faham)
**bermacam-macam jenis encryption yang ada kat dunia nih.. wal hal kita pun bleh buat sendiri.. wink;)**
ok apa yang bagusnya encryption nih??
- is the good way to save ur emel or fb password without anyone can guess if u doing ur own encryption is .. (bestkan??)
- eg: shedah to WKHNjj801 (ko yg buat ko je yang tau)
- ok other benefit is when u sms or emel or post wall/comment in fb to ur lover, u can use encryption then no one didnt know what the message is.. hahaha
- other thing is not good thing ok... u can use encryption to gossip with ur friends,, ha interesting rite?? but dont do this at home.. is not pratical n unhealthy way why u juz straight to her and talk what ever u want.. (hahahahah orang nk omputih ang pun nk jgak dh tu gasak , )))
HASHING
Hashing is used only to verify data; the original message cannot be retrieved from a hash. When used to authenticate secure communications, a hash is typically the result of the original message plus a secret key. Hashing algorithms are also commonly used without a secret key simply for error checking. You can use the md5sum and sha1sum utilities on a Linux or Unix machine to experiment with hashing.
$ echo -n This is a secret message. | md5sum39de572a4d05b1ad6552dcfee90f4d20 -$ echo -n This is a secret message. | sha1sume35c5046b5fe69488ce0ab14c5761d785995ee79 -***(ayat yang mudah difahami adalah hashing ini menggunakan sehala jalan sahaja)***
SYMMETRIC ENCYRPTION
Symmetric encryption may also be referred to as shared key or shared secret encryption. In symmetric encryption, a single key is used both to encrypt and decrypt traffic.
Common symmetric encryption algorithms include DES, 3DES, AES, and RC4. 3DES and AES are commonly used in IPsec and other types of VPNs. RC4 has seen wide deployment on wireless networks as the base encryption used by WEP and WPA version 1.
Symmetric encryption algorithms can be extremely fast, and their relatively low complexity allows for easy implementation in hardware. However, they require that all hosts participating in the encryption have already been configured with the secret key through some external means.
***(ayat yang mudah difaham adalah symmetric ini menggunakan satu jenis kunci sahaja untuk encrpyt dan decrypt)***
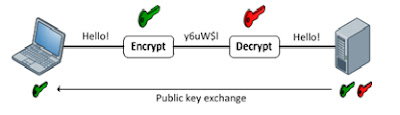
ASYMMETRIC ENCRYPTION
Asymmetric encryption is also known as public-key cryptography. Asymmetric encryption differs from symmetric encryption primarily in that two keys are used: one for encryption and one for decryption. The most common asymmetric encryption algorithm is RSA.
Compared to symmetric encryption, asymmetric encryption imposes a high computational burden, and tends to be much slower. Thus, it isn't typically employed to protect payload data. Instead, its major strength is its ability to establish a secure channel over a nonsecure medium (for example, the Internet). This is accomplished by the exchange of public keys, which can only be used to encrypt data. The complementary private key, which is never shared, is used to decrypt.
Robust encryption solutions such as IPsec implement the strengths of both symmetric and asymmetric encryption. First, two endpoints exchange public keys, which allows for the setup of a slow but secure channel. Then the two hosts decide on and exchange shared symmetric encryption keys to construct much faster symmetric encryption channels for data.
***( ayat yang mudah difahami assymmetric ini menggunakan dua kunci iaitu encrpyt menggunakan kunci lain dan decrypt menggunakan kunci lain)***
SEKIAN....



No comments:
Post a Comment